70以上 ninja-tools access control counter 338054-Ninja-tools access control counter 回避
Top of Page Change a bound control to a calculated control A good way to create a calculated control is by first creating a bound control (for example, by dragging a field from the Field List pane to your form or report), and then editing the bound control's Control Source property to create an expression This works well, as long as you ensure that the name of the control does not conflictAccess control systems are among the most critical of computer security components Faulty policies, misconfigurations, or flaws in software implementations can result in serious vulnerabilities To formally and precisely capture the security properties that access control should adhere to, access control models are usually written, bridgingAccess control sounds like a simple problem but is insidiously difficult to implement correctly A web application's access control model is closely tied to the content and functions that the site provides In addition, the users may fall into a number of groups or roles with different abilities or privileges

Ninja Tools Access Control Counter
Ninja-tools access control counter 回避
Ninja-tools access control counter 回避-Access control sounds like a simple problem but is insidiously difficult to implement correctly A web application's access control model is closely tied to the content and functions that the site provides In addition, the users may fall into a number of groups or roles with different abilities or privilegesA view's visibility properties determines the access control mechanism that is applied to the business component on which the view is based For example, the business component might have personal or position access control available The view specifies which of these to use, and in which form to use it



11 Best Ninja Foodi Accessories That I Use In My Kitchen The Salted Pepper
AC00 Instant Data Export Tool The AC00 Instant Data Export Tool process is a perfect solution for lowlevel integration where Security Management System database changes are automatically reported to third party systems such as Human Resources or Enterprise Resource PlanningAccess Control applications present unique challenges that often require sensorbased solutions to effectively manage pedestrian traffic BEA's access control line includes a variety of products that can be combined to create allinone packages designed to enhance employee safety and securityThe XP tracker (formerly known as the XP Counter or XP ticker) was originally released by Jagex to members along with the Bonus XP Weekend on 12 March 10 Exactly one month later on 12 April 10, it was released to all players It did not get very much attention because it was publicized in the same announcement that unveiled the highlyanticipated skill, Dungeoneering
問答無用でninjatools access control counterに飛ばされます。 戻れません。 NoScriptで、そのblogだけジャバスクリプト解禁しようにも飛ばされた先では意味がありません。With organizations now having to account for exponential growth of mobile devices accessing their networks and the security risks they bring, it is critical to have the tools that provide the visibility, access control, and compliance capabilities that are required to strengthen your network security infrastructureOccupancy Tracker Tool,Access Management,Capacity Control HeadCounter is a capacity management tool that allows you to keep track of how many people go in and out of events, hotels or any other public spaces you may have
IBM's Identity and Access Management lets you authenticate the users and control the access to resources across the cloud platform Its main features include single enterprise signon, accessDavid Ferraiolo and Rick Kuhn in their book Role Based Access Control proposed the RBAC model based on the premise that it reduces the overall cost of maintaining secure access control That model has since been adopted as an ANSI/INCITS standard ANSI/INCITS standard Role based access control is not a mandatory access control (MAC) nor is it a discretionary access control (DAC)The breach prevention and detection market is dominated by names like Symantec, McAfee and Juniper, but open source tools are also popular



Esg Technical Validation Google Cloud Security For Data Analytics



Army Selects Countermeasures Against Drones Article The United States Army
In the Control Source property box, type =Count(*) This expression uses the Count function to count all the records in the report or group even if some fields in some records are null To count records only where a specific field is not null (for example, SupplierName), use the following expression instead =CDbl(Nz(Count(SupplierName),0))問答無用でninjatools access control counterに飛ばされます。 戻れません。 NoScriptで、そのblogだけジャバスクリプト解禁しようにも飛ばされた先では意味がありません。Insert a page break control You can insert a page break in sections other than the Page Header and Page Footer sections of a report For example, to print a report's title page on a separate page, place the page break in the Report Header section after controls that you want to appear on the title page In the example below, the page break control is between the header and the description



3e9af81ctrccrm
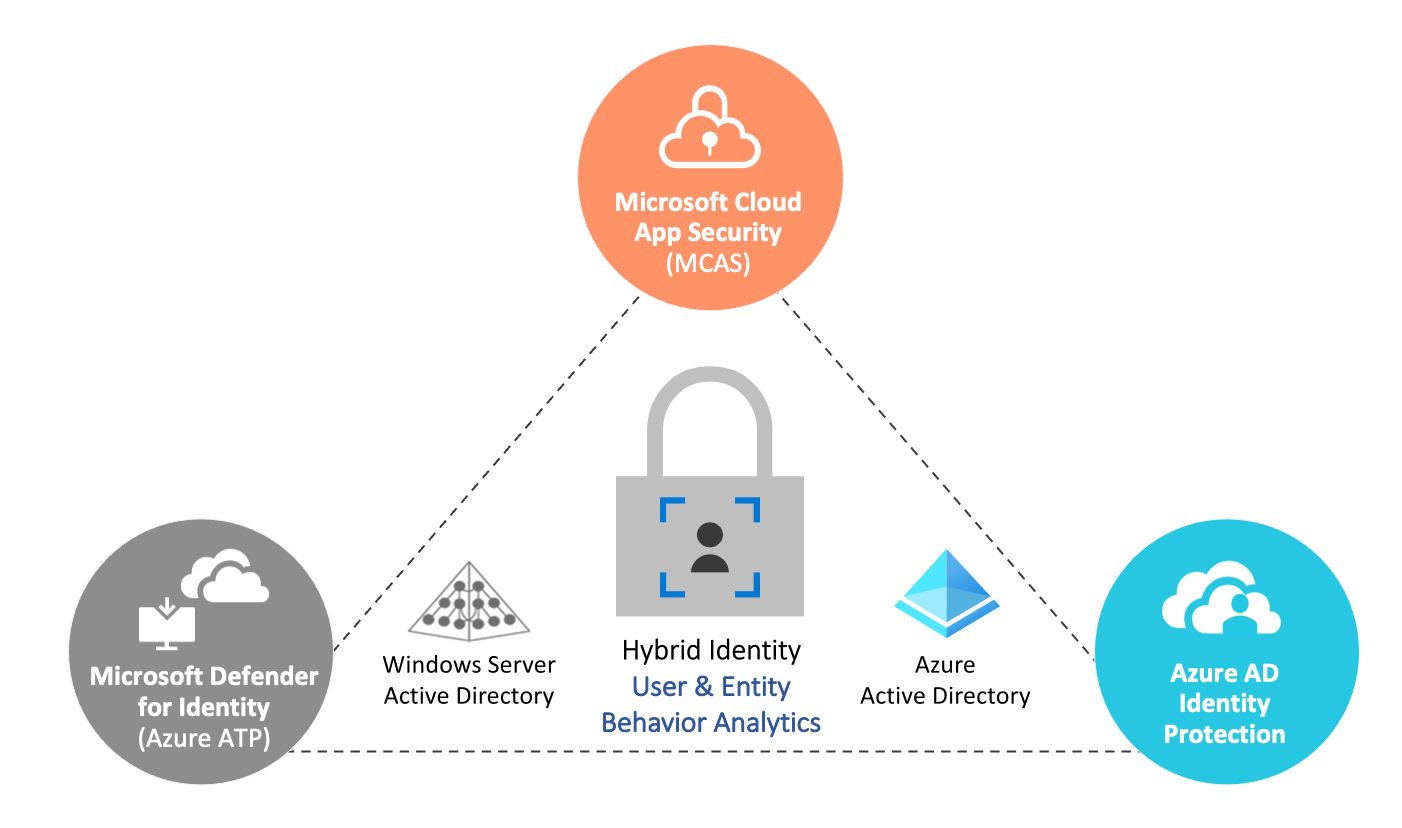


Cloud Architekt Net Identity Security Monitoring In Microsoft Cloud Services
Access control (AC) systems control which users or processes have access to which resources in a system They are among the most critical of security components AC policies are specified to facilitate managing and maintaining AC systems Faulty policies, misconfigurations, or flaws in software implementations can result in serious vulnerabilitiesBEA is the industry leader in research, development & integration of sensing solutions for pedestrian, industrial, transportation & security applicationsElevator machine rooms and control roomsExit access doorways shall be provided from elevator machine rooms and control rooms when required by Section 2734 of ASME A 171 as referenced in rule of the Administrative Code Egress from stories or occupied roofs



Us Army Selects Future Counter Uav Systems Atlantic Organization For Security Aos
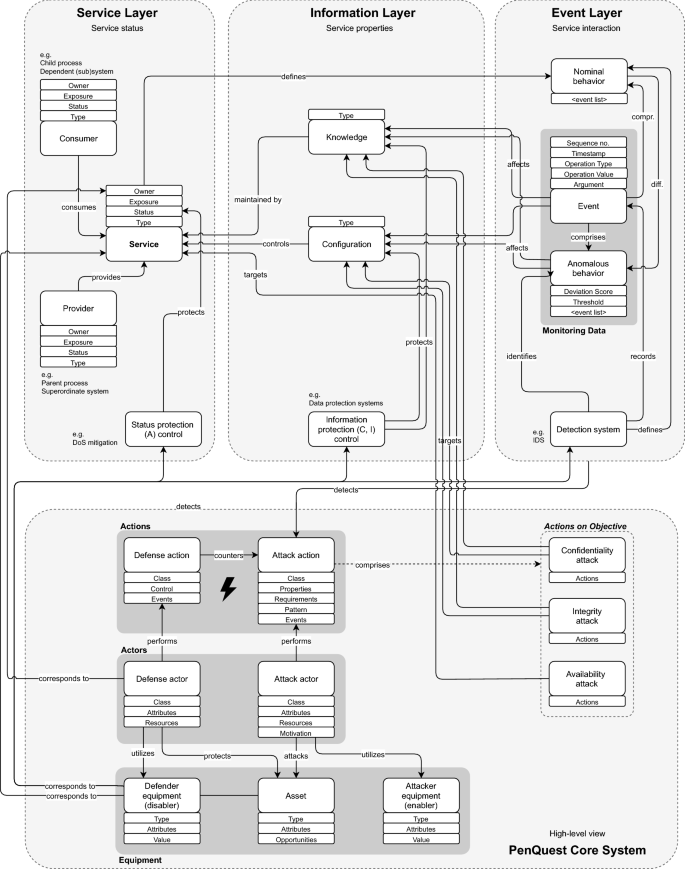


Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink
Security Control #1 Inventory of Authorized & Unauthorized Devices Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining accessShop Ninja Smart Screen 72Oz Blender Black at Best Buy Find low everyday prices and buy online for delivery or instore pickup Price Match GuaranteeSourceSecuritycom, the complete industry guide Find Inner Range Insight Enterprise or any electronic security product from the extensive ,000 products in the database, make sales enquiries, order literature requests, download datasheets and make full use of SourceSecuritycom's marketing services



This Appliance Replaced Everything On My Kitchen Counter Real Simple



Ninja Smart Screen Review Rtings Com
Different tools are used for different problemsolving opportunities, and many of the tools can be used in different ways The trick is to become familiar and comfortable with all of these quality tools so you can pull the appropriate one out of your toolbox when there is a problem that needs to be solved 7 Management Tools For Quality Control 1Hobbysupplyblogshinobijp NINJATOOLS ACCESS CONTROL COUNTER Offline Hobbysupplyblogshinobijp visit the most interesting Hobbysupply Blog Shinobi pages, wellliked by users from Japan, or check the rest of hobbysupplyblogshinobijp data below Hobbysupplyblogshinobijp is a web project, safe and generally suitable for all agesJIRA user management and access control Jirong Hu Mar 27, 15 I am a bit confused by access control in JIRA now We have integrated JIRA with AD and have these standard AD groups, jirausers, jiradevelopers, jiraadministrators, jirapowerusers I see either these groups and individual users has been added to roles in projects



5 Current Cyber Attack Techniques And How To Stay Threat Informed



Best Blenders 21 Cnn Underscored
Access Rights Management (ARM), also known as access control or simply access management, is the practice of ensuring people in an organization have appropriate access to technology resources Good access management tools ensure your users can access areas of your network/systems needed to do their job whilst ensuring other areas are kept offlimits in orderSecurity Control #1 Inventory of Authorized & Unauthorized Devices Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining accessOpenpath access control integrations Openpath's open platform allows you to create a complete solution that works with all the apps and tools you need to run your business We support a wide range of everyday apps right out of the box with minimal setup required and easily integrate with peripheral hardware, including other legacy access



Amazon Com Ninja Professional 72 Oz Countertop Blender With 1000 Watt Base And Total Crushing Technology For Smoothies Ice And Frozen Fruit Bl610 Black Kitchen Dining



Wireshark User S Guide
Testing should frequently be done on the access control systems, for example, like whenever a new control is deployed, or a new logical network segmentation is performed Testing results should be distributed, and appropriate decisions should be made to fine tune the existing policies or create a new policy if one is missingControlled Access is a family run business with family instilled values Quality, reliability, durability and customer service For over 30 years, we've been building our globally trusted turnstiles right here in Ohio and shipping them to professional sports and entertainment venues, manufacturing facilities, universities, military sites andBB SMARTWORX 1 Industrial Communication and Control 139;



Amazon Com Ninja Professional Countertop Blender With 1100 Watt Base 72 Oz Total Crushing Pitcher And 2 16 Oz Cups For Frozen Drinks And Smoothies Bl660 Gray Electric Countertop Blenders Kitchen Dining
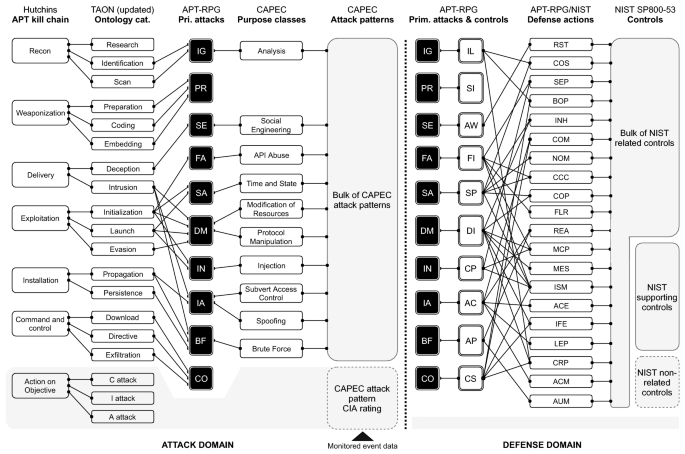


Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink
Ninja appears to have concluded that any counter space their products demand had better offer lots of functionality An appliance that can turn out smoothies or soups, knead dough or chop salad ingredients, and serve up a variety of desserts will earn its place on our kitchen counter NINJA is a clever companyAccess control systems aim to control who has access to a building, facility, or a "for authorized persons only" area This is typically carried out by assigning employees, executives, freelancers, and vendors to different types of groups or access levelsThis topic for the IT professional describes access control in Windows, which is the process of authorizing users, groups, and computers to access objects on the network or computer Key concepts that make up access control are permissions, ownership of objects, inheritance of permissions, user rights, and object auditing



Ninja Foodi Power Blender Processor System With Smoothie Bowl Maker And Nutrient Extractor Series Official Ninja Product Support Information



Top 13 Wordpress Project Management Plugins And Tools 21
SERVICES Life Long Craftsman Woodwork, installation, repairs, and more My services might be varied, but they all come with the same promise of quality, dedication, and durabilityAccess Control System Software free download LightScribe System Software, Access 07 Download Access Runtime, DownloadX ActiveX Download Control, and many more programsAccess Control System Software free download LightScribe System Software, Access 07 Download Access Runtime, DownloadX ActiveX Download Control, and many more programs



Ninja Tools Access Control Counter あしゅ 齋藤飛鳥 斉藤飛鳥



Ninja Tools Access Control Counter
1 The Ninja 2 Creating a Ninja 21 Quick Build 3 Class Features 31 Table The Ninja 32 Deadly Handling 33 Fighting Stance 331 Bear Stance 332 Cheetah Stance 333 Eagle Stance 334 Eel Stance 335 Mantis Stance 336 Turtle Stance 34 Unarmored Defense 35 Spellcasting 36 Concealed Tools 37 Shinobi's Shadow 38 Ability Score Increase 39 Rapid Throw 310 Extra Attack 311 UnnaturalThe Automated Border Control Gate is an automated immigration control product – developed in partnership with Gemalto and Automatic Systems both leaders in biometrics and access control markets – combining the latest technologies of electronic gate hardware and border control softwareAccess groups RoleBased Access Control (RBAC) • Information will be repeatedly shared with that particular group • Group membership information is normally visible to all members of an organization • Lack of transparency 1 or at least repeatedly enough to offset the effort required for group creation


Www Gigamon Com Content Dam Resource Library English Analyst Industry Report Cyber Security Annual Cyber Security Handbook And Reference Guide Vol 3 Pdf



The Best Blenders Of 19 Breville Ninja Kitchenaid And More
Assuming the publisher could get past the challenge of adding accesscontrol data to their usage reporting, the inclusion of zerouse titles in Book Reports or even Journal Reports where yearofpublication data is tracked could result in COUNTER reports that are hundreds of thousands or even millions of rows longCSM Review says Forescout's CounterACT 8 is a powerful and highly scalable network visibility and access control solution that delivers the best classification tools for instant awareness of all networkconnected devices Download COUNTERACT 8 WEBINAR SERIESWith the form in Design view, insert a text box control Enter the expression in the form =Count (primarykey) as the control's Control Source property The Count () function takes just one


忍者バリアーを簡単にピンポイントで回避 解除 する方法 Firefox アドオン Adblock Plus を利用 pcプチ技能向上委員会



Ninja Foodi Review The Gadget That Could Replace Your Instant Pot And Air Fryer Reviewed
Access Control Software Innovative Solutions for Securing Commercial Environments of Any Size Due to an exponential growth in foot traffic within many commercial businesses, implementing a robust security system for access control and user credential authentication is indispensableBOSCH SECURITY SYSTEMS 766 Access Control;PELCO 2109 Access Control 3



Ninja Professional Plus Kitchen System With Auto Iq Black Stainless Steel Bn801 Best Buy



Amazon Com Ninja Foodi Ag301 5 In 1 Indoor Electric Countertop Grill With 4 Quart Air Fryer Roast Bake Dehydrate And Cyclonic Grilling Technology Kitchen Dining
Step 1 If you have not installed EZTools already, click here to navigate to the UniView download section and download the latest version of EZTools shown on the page After EZTools has successfully installed, click on your Windows Start button or tap on your Windows Key In your Start menu, either start typing "EZTools" or navigate to the EZTools folder and find the shortcut to launch theAccess control systems aim to control who has access to a building, facility, or a "for authorized persons only" area This is typically carried out by assigning employees, executives, freelancers, and vendors to different types of groups or access levelsWhat is access rights management?



Ninja Tools Access Control Counter 生田絵梨花 生田 桜井


October 19 Xbox Game Bar Update Enables Fps Counter And Achievement Tracking Xbox Wire
Click the Data tab In the Control Source property box, type the field name or expression for which you want to create the running sum For example, type ExtendedPrice for the ExtendedPrice field or, at the group level, type the expression =Sum ( ExtendedPrice) Click the Running Sum property boxWhy is it important to have a NAC solution?A popular tool for information access control is a virtual private network (VPN) A VPN is a service that allows remote users to access the Internet as though they were connected to a private network Corporate networks will often use VPNs to manage access control to their internal network across a geographic distance



Super Crispy Air Fryer Bacon Recipe Erhardts Eat


Reverse Engineering Attacks 6 Tools Your Team Needs To Know Techbeacon
Access Control Devices •Access control authenticates, authorizes users –Authentication validate a person's identity –Authorization specify what the person can do with computers, networks –Recommended use ≥ two types of auth technology •Four main ways to authenticate person –What a person knows (eg, password);Access control systems are the electronic systems that are designed to control through a network and they should have an access to a network Access Control System recognizes authenticates and authorizes entry of a person to enter into the premise thereby giving complete protection ensuring security with the system



Amazon Com Modern Ninja Warfare Ninja Tactics For The Modern Warrior Ebook Cummins Antony Kane Jayson Kindle Store



Ninja Tools Access Control Counter



Pearl Drums P50c Eliminator Redline Bass Drum Pedal Chain Drive Ninja Bearings



Ninja Foodi Digital Air Fry Oven Review Here S How It Actually Works Reviewed



Ninja Tools Access Control Counter



The Ninja Foodi Digital Air Fry Oven Is Off On Amazon Food Wine



Ninja Mega Kitchen System Bl770 Review Rtings Com



Seo Tools The Complete List 21 Update



Ninja Tools Access Control Counter
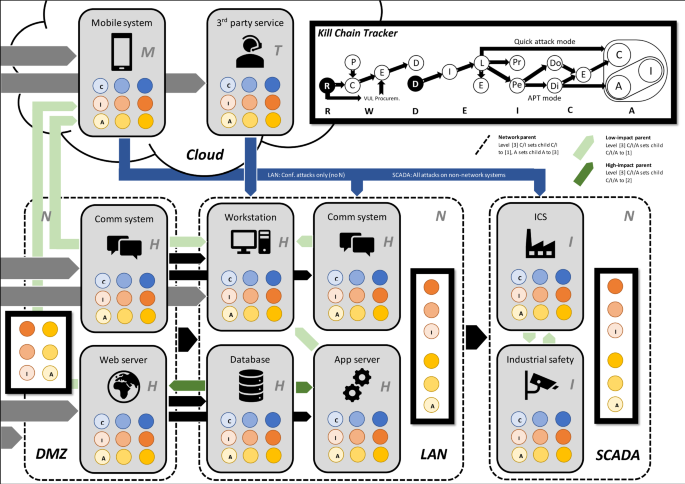


Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink



Ninja Tools Access Control Counter



11 Best Ninja Foodi Accessories That I Use In My Kitchen The Salted Pepper



Army Selects Countermeasures Against Drones Article The United States Army



Ninja Professional Plus Kitchen System With Auto Iq Review Rtings Com



Naruto Shippuden Ultimate Ninja Storm Revolution Narutopedia Fandom


Field Types Ninja Forms



Naruto Shippuden Ultimate Ninja Storm 4 Beginner Tips And Tricks Naruto Shippuden Ultimate Ninja Storm 4



Naruto Slugfest Guide Tips Cheats Strategies To Increase Cp Mrguider



Ninja Professional Plus Kitchen System With Auto Iq Black Stainless Steel Bn801 Best Buy



5 Current Cyber Attack Techniques And How To Stay Threat Informed



Ninja Coffee Bar System Cf097 Walmart Com Walmart Com
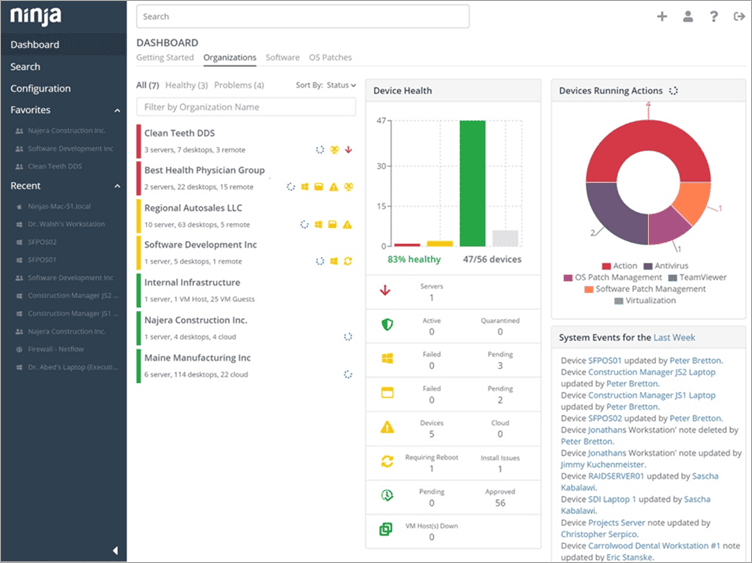


Top 10 Best System Monitoring Software Tools 21 Selective



Ninja Tools Access Control Counter 美容 美髪 オルチャンガール



Wireshark User S Guide


1


Www Usenix Org System Files Conference Usenixsecurity17 Sec17 Ning Pdf


The Future Is Now Our New Client Area And Site Tools Are Going Live Siteground Blog


Github Kdeldycke Awesome Iam Identity And Access Management Knowledge For Cloud Platforms



Ninja Tools Access Control Counter



Ninja Stainless Steel Foodi Digital Air Fry Oven Convection Oven Toaster Air Fryer Flip Away For Storage Sp101 The Home Depot


Q Tbn And9gcqczujcnvzcwht2fcaj8lna0uavastt Iq4n2da I4 Incb0fv Usqp Cau



ボード 乃木坂 のピン



Foods Co Ninja Dt1 Foodi Air Fryer 1 Ct


Http D1vtv52f4vjbmu Cloudfront Net Manuals Ns4 Rtb Pc Manualonline Naruto Pc Gbqs Hr Pdf



Best Ninja Coffee Makers The Bar And Other Brewers
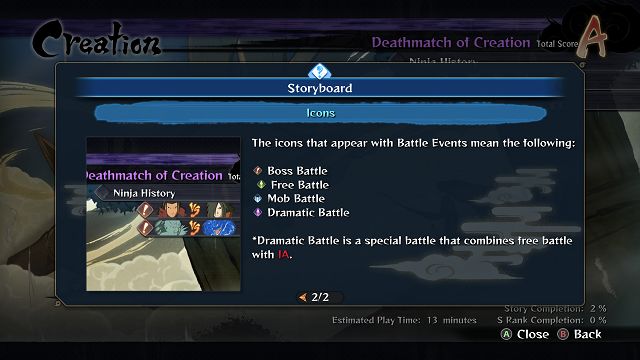


Naruto Shippuden Ultimate Ninja Storm 4 Beginner Tips And Tricks Naruto Shippuden Ultimate Ninja Storm 4



Amazon Com Ninja Sp101 Foodi 8 In 1 Digital Air Fry Large Toaster Oven Flip Away For Storage Dehydrate Keep Warm 1800 Watts Xl Capacity Stainless Steel Kitchen Dining



Ninja Tune Wikipedia



Amazon Com Ninja Foodi Ss1 Power Blender Processor 3 In 1 Crushing Blender Dough Mixer And Food Processor 1400wp Smarttorque 6 Auto Iq Presets Kitchen Dining



Ninja Foodi Power Pitcher System Review Rtings Com


Does Tenten From Naruto Have The Capability To Be The Strongest Ninja Ever Quora



Ninja Stainless Steel Foodi Digital Air Fry Oven Convection Oven Toaster Air Fryer Flip Away For Storage Sp101 The Home Depot



Ninja Sp101 Foodi 8 In 1 Digital Air Fry Oven Walmart Com Walmart Com



Ninja Coffee Brewer Montgomery Ward



It Campus Security College And School Campus Education Security Security Today


Ninja 4 Megapixel Ip Dome Camera 16 Ch Kit



Ninja Tools Access Control Counter 中村麗乃 美人 顔 中村



Ninja Tools Access Control Counter


Does Tenten From Naruto Have The Capability To Be The Strongest Ninja Ever Quora



Top 13 Wordpress Project Management Plugins And Tools 21



Ninja Stainless Steel Foodi Digital Air Fry Oven Convection Oven Toaster Air Fryer Flip Away For Storage Sp101 The Home Depot



Kbr Wins 92 6m Contract To Reinforce The U S Navy S Counter Unmanned Air Systems Strengthens National Defense


Versprite S Analysis Of A Vulnerable Window Named Pipe Application



Katasuke Tōno Narutopedia Fandom


Q Tbn And9gcs Mfgasz3v7 Lfrit29phlycpaf0rblozuzosomne Usqp Cau



P 7gnzuscj6 Xm


Ninja Sp101 Foodi 8 In 1 Digital Air Fry Oven Flip Away For Storage Dehydrate Keep Warm Bed Bath Beyond


Best Log Management Tools 51 Useful Tools For Log Management Monitoring Analytics And More Stackify



Ninja Tools Access Control Counter 顔 ジャパニーズビューティー 美人 顔


Versprite S Analysis Of A Vulnerable Window Named Pipe Application
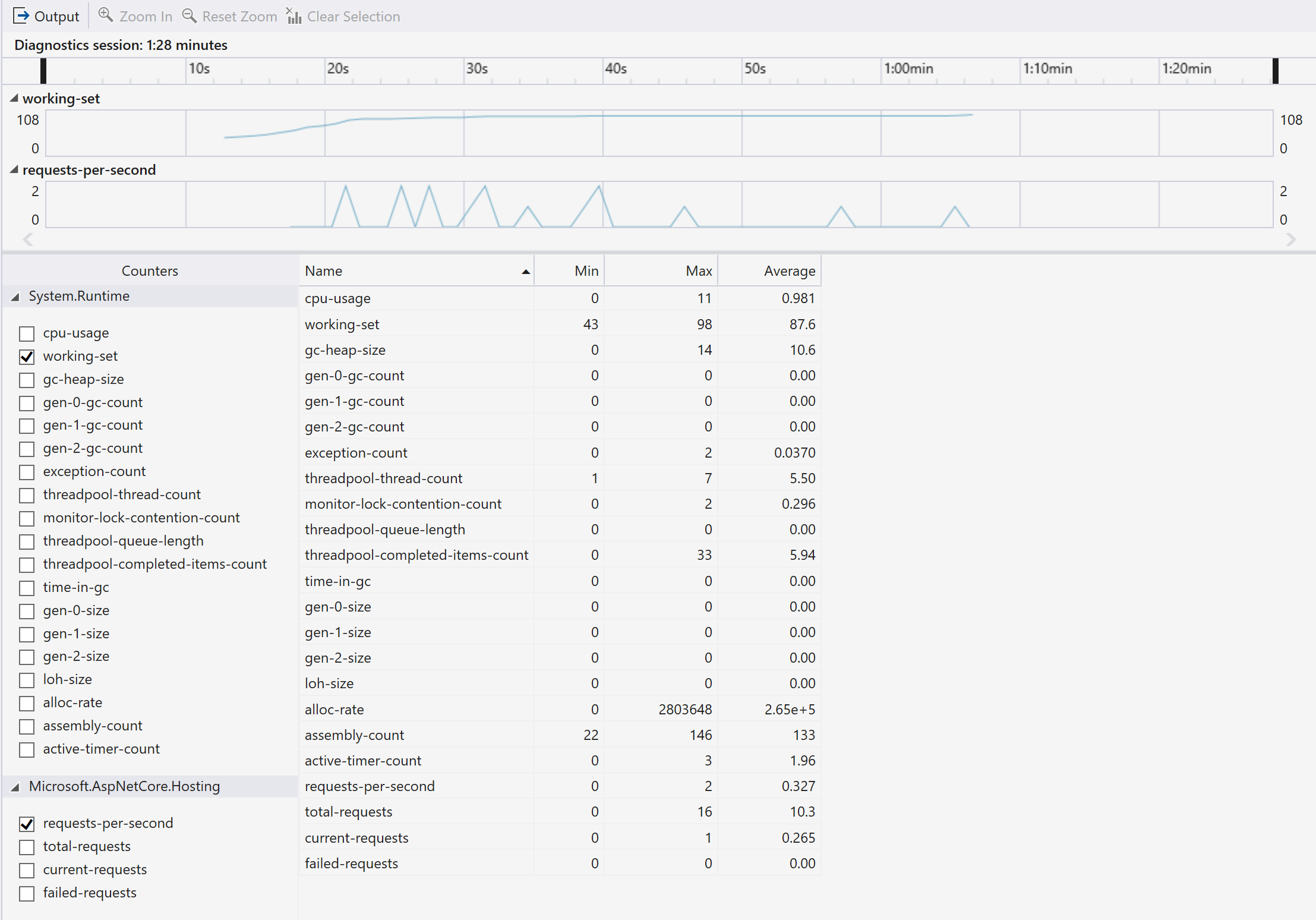


Visual Studio 19 Version 16 7 Release Notes Microsoft Docs



Foods Co Ninja Dt1 Foodi Air Fryer 1 Ct



Microsoft Security



Security Experts Say Drones Pose A National Security Threat Time


Cloud Architekt Net Identity Security Monitoring In Microsoft Cloud Services


Q Tbn And9gcqczujcnvzcwht2fcaj8lna0uavastt Iq4n2da I4 Incb0fv Usqp Cau



Esg Technical Validation Google Cloud Security For Data Analytics



Ninja Tools Access Control Counter



Ninja Tools Access Control Counter



Ninja Tools Access Control Counter 久保 久保史緒里



Ninja Tools Access Control Counter



Ninja Tools Access Control Counter



Jwieugcs70aywm


Conf Splunk Com Files 17 Slides Security Ninjutsu Part Four Attackers Be Gone In 45 Minutes Of Epic Spl Pdf



Skill Trees In Nioh 2 Nioh 2 Guide Gamepressure Com



Amazon Com Ninja Bl770 Mega Kitchen System And Blender With Total Crushing Pitcher Food Processor Bowl Dough Blade To Go Cups 1500 Watt Base Black Electric Countertop Blenders Kitchen Dining


コメント
コメントを投稿